Polygraf AI closes $9.5M Seed Round led by Allegis Capital
Polygraf AI closes $9.5M Seed Round led by Allegis Capital
We check your text against billions of sources to confirm it’s truly original.











Summerfest Tech
Best Fin/Insurtech 2025
2025
SXSW
Best in Show
2025
SXSW PITCH
Enterprise, Smart Data, FinTech & Future of Work
2025
Product That Count
Top AI & Data Category Product
2025
SXSW
Top 10 Startup Of The Year 2024
2024
dealroom.co
Top Analytics Startup to Watch for Globally
2024
Nvidia
NVIDIA Inception Program Member
2024
Product That Count
Top AI & Data Governance Product
2024
Product That Count
Top AI Content Detection Tool
2024
C2PA
Contributing Member
2024
Intel
Intel Alliance Program Member
2024
Austin Chamber
Top AI Startup
2023
Unattributed use of existing content undermines trust and can lead to legal and reputational risks.
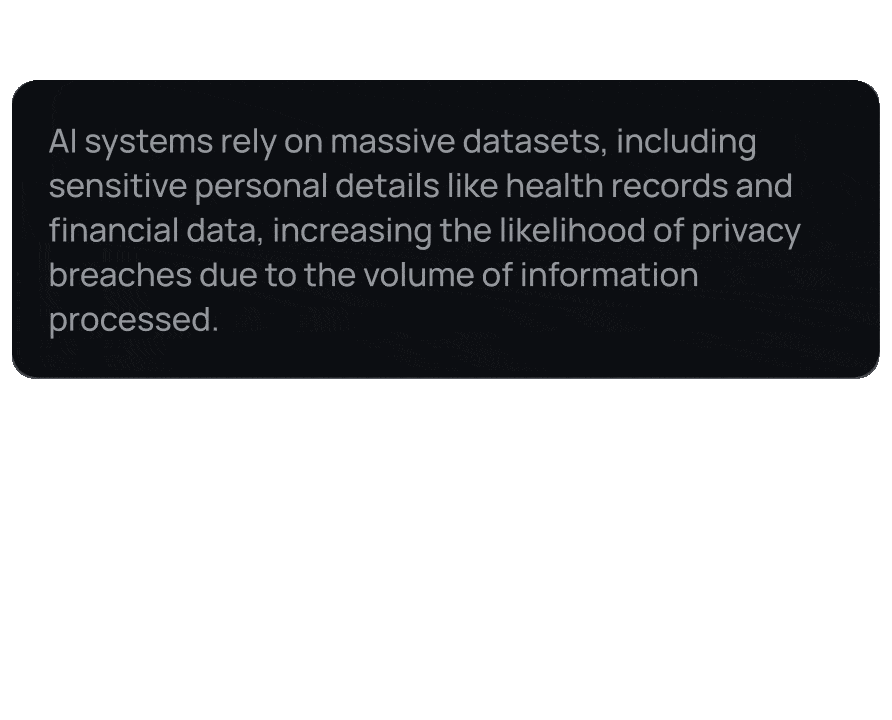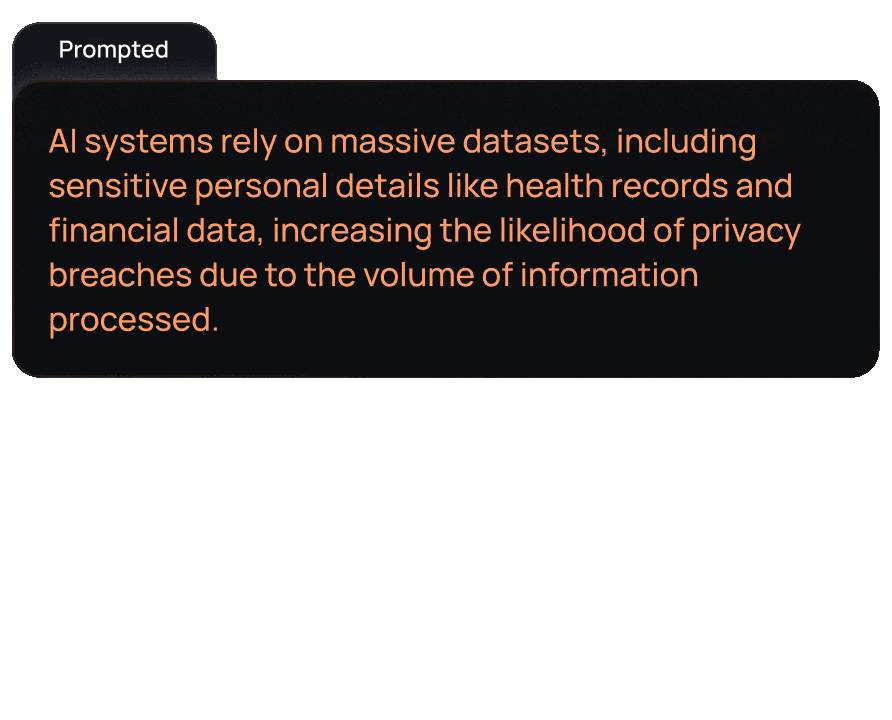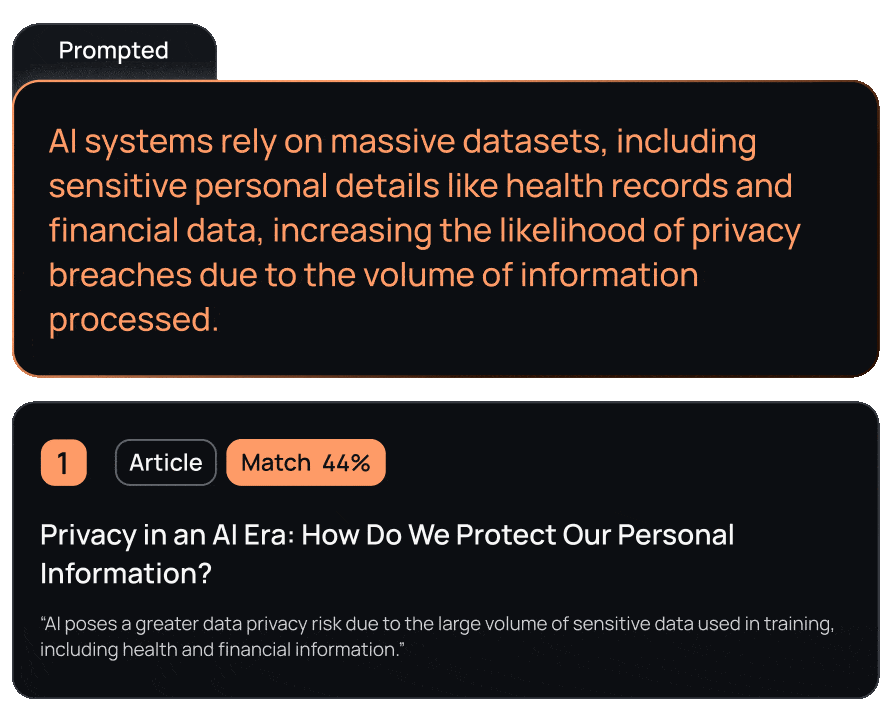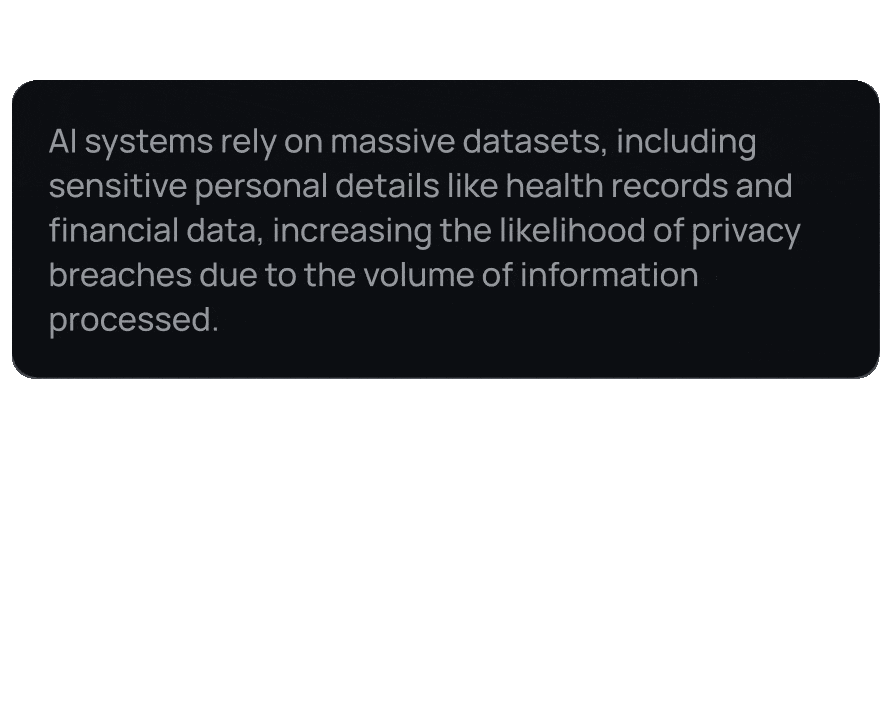
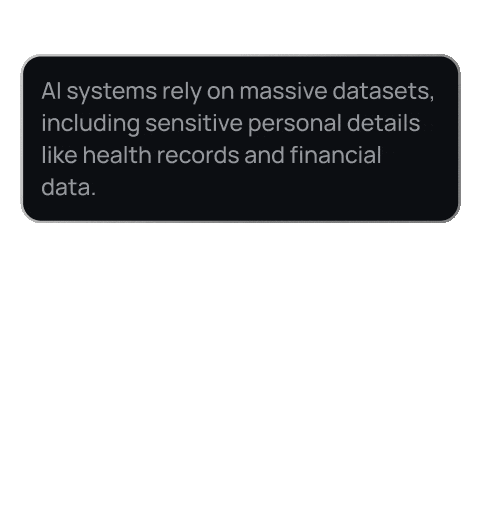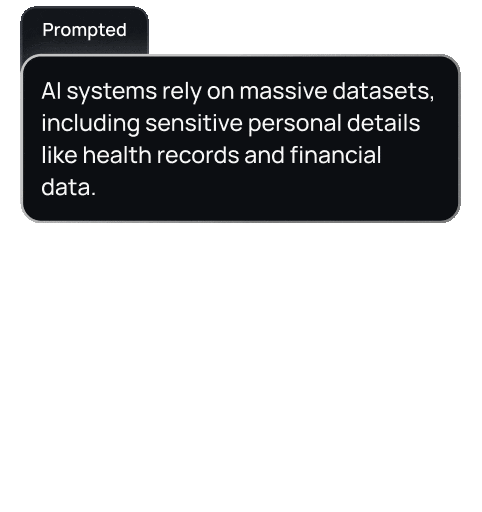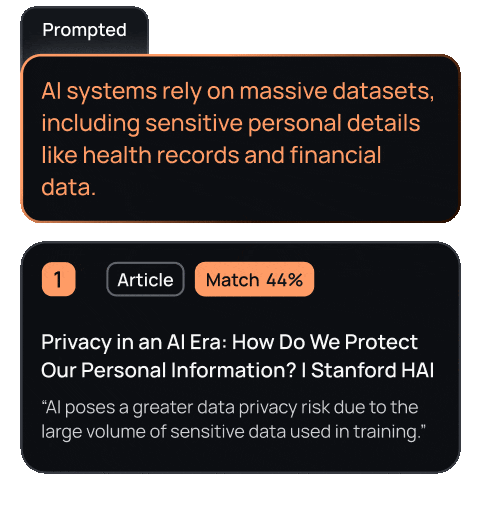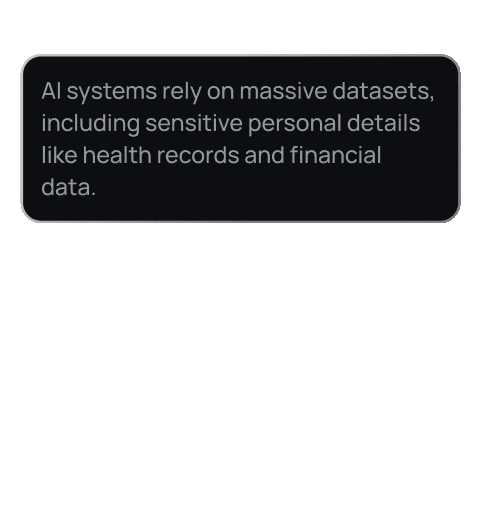
Our Plagiarism Detector identifies instances of plagiarism by comparing text against billions of web pages, academic papers, books, and articles. It highlights exact matches and paraphrased passages, providing detailed source information and similarity percentages. This enables organizations to uphold content integrity and ensure proper attribution.
Our tools use advanced encryption and access controls to ensure only authorized users can access sensitive data, reducing the risk of data breaches.
Stay compliant with global data privacy regulations like GDPR, HIPAA, and CCPA by automatically identifying and protecting sensitive information.
Automate the detection and management of PII, saving time and resources that would otherwise be spent on manual data auditing and redaction.
It scales and handles large volumes of data and multiple users efficiently, ensuring consistent data privacy across your entire ecosystem.
Identify which AI models were used to generate content.
Identify copyrighted material and avoid legal complications.
Automatically highlight parts of text that are AI-generated.
Maintain content integrity and ensure proper attribution.
Spot human edits in AI-Generated content.
Analyze writing patterns to maintain consistent voice and quality.
Detect synthetic voices and AI-created audio.
Identify which AI models were used to generate content.
Identify copyrighted material and avoid legal complications.
Automatically highlight parts of text that are AI-generated.
Maintain content integrity and ensure proper attribution.
Spot human edits in AI-Generated content.
Analyze writing patterns to maintain consistent voice and quality.
Detect synthetic voices and AI-created audio.
Data Provenance tools are included in all Plans.
Identify which AI model generated your content, showing human vs. AI percentages and grammar enhancements.
Detect copyrighted content, showing percentages, URLs, and text.
Highlight text as AI-generated (red), human-generated (green), or altered (yellow) for easy verification.
Verify originality, showing plagiarism sources and percentages.
Identify which AI model generated your content, showing human vs. AI percentages and grammar enhancements.
Identify which AI model generated your content, showing human vs. AI percentages and grammar enhancements.
Identify which AI model generated your content, showing human vs. AI percentages and grammar enhancements.
© 2025 Polygraf AI. All rights reserved.
Your download will start now.
Please provide information below and we will send you a link to download the white paper.